Why you shouldn't PermitRootLogin: Pwning the Doubledouble.top / GamesDrive reverse proxy
R O O T P A S S W O R D I N B I O
So I was minding my business playing Warframe when my friend texted me this.
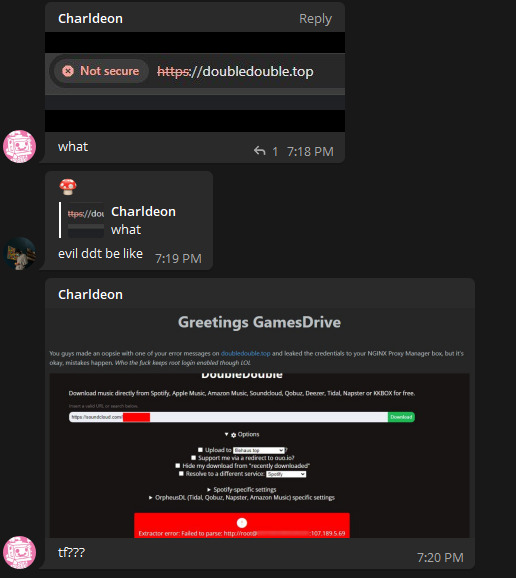
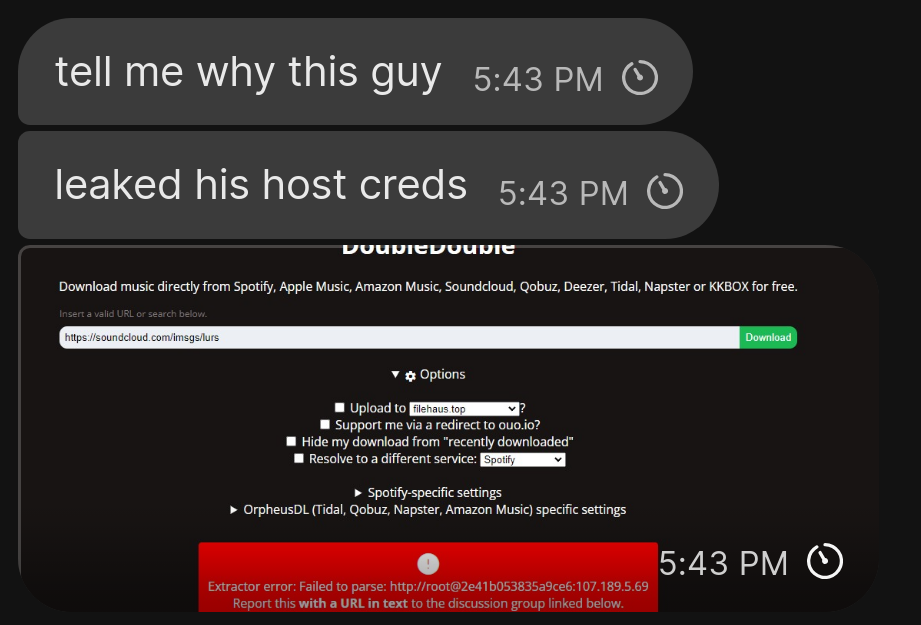 An error message from doubledouble.top, leaking the root credentials to, something. I thought this was fucking hilarious, but he had signed in via SSH asking me what to do with it, so of course I took a look. After a bit of investigating, I had discovered it was a Debian machine running Nginx Proxy Manager in a Docker container.
An error message from doubledouble.top, leaking the root credentials to, something. I thought this was fucking hilarious, but he had signed in via SSH asking me what to do with it, so of course I took a look. After a bit of investigating, I had discovered it was a Debian machine running Nginx Proxy Manager in a Docker container.
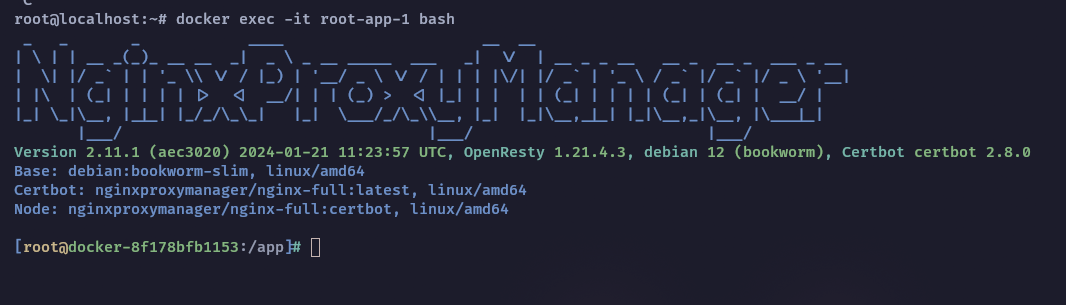 I had never used Nginx Proxy Manager before , so I seek the documentation and learn that in a default configuration it exposes an admin panel at port
I had never used Nginx Proxy Manager before , so I seek the documentation and learn that in a default configuration it exposes an admin panel at port 81 and stores an SQLite database at the /data volume.
 Well, here it is, what now?
Well, here it is, what now?
Pwnage
Well, let's inspect the SQLite database.
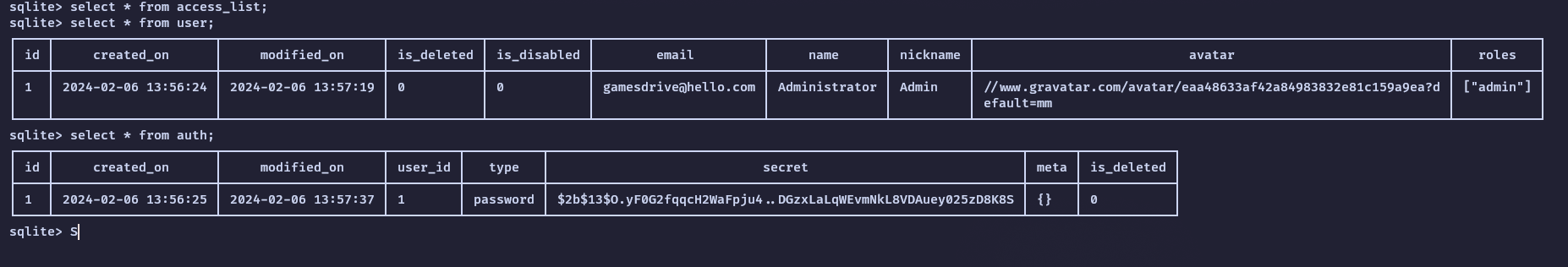 We find an administrator at id
We find an administrator at id 1 and the email gamesdrive@hello.com, and a bcrypt hash for user_id 1. At first I was confused about the email address, because it was not known to me that https://www.doubledouble.top and https://gamesdrive.net were affiliated. I moved on and realized how I could log in as Admin, just update the bcrypt hash. I install the sqlite command line in the Docker container and generate a bcrypt hash with the mkpasswd command on my Linux machine, and a simple sqlite shell command should do the trick.
UPDATE auth SET secret = "<new_hash>" WHERE id = 1;
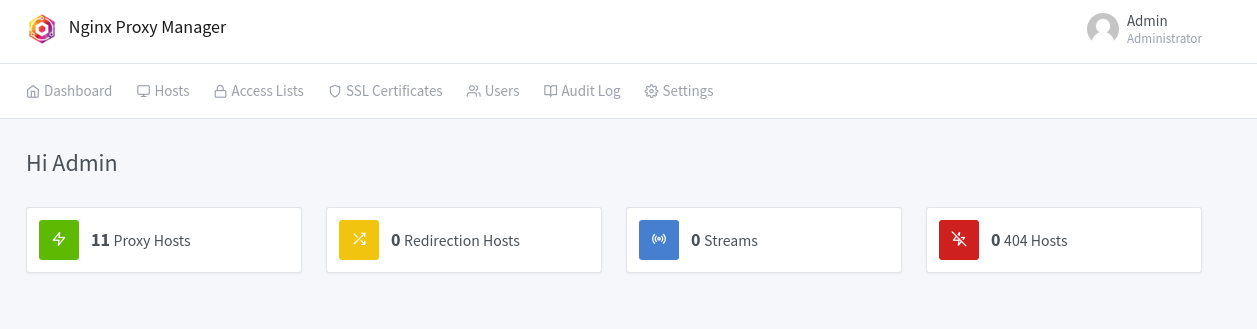 And we're in. Now let's go check out those proxy hosts, because 11 is a pretty big number.
And we're in. Now let's go check out those proxy hosts, because 11 is a pretty big number.
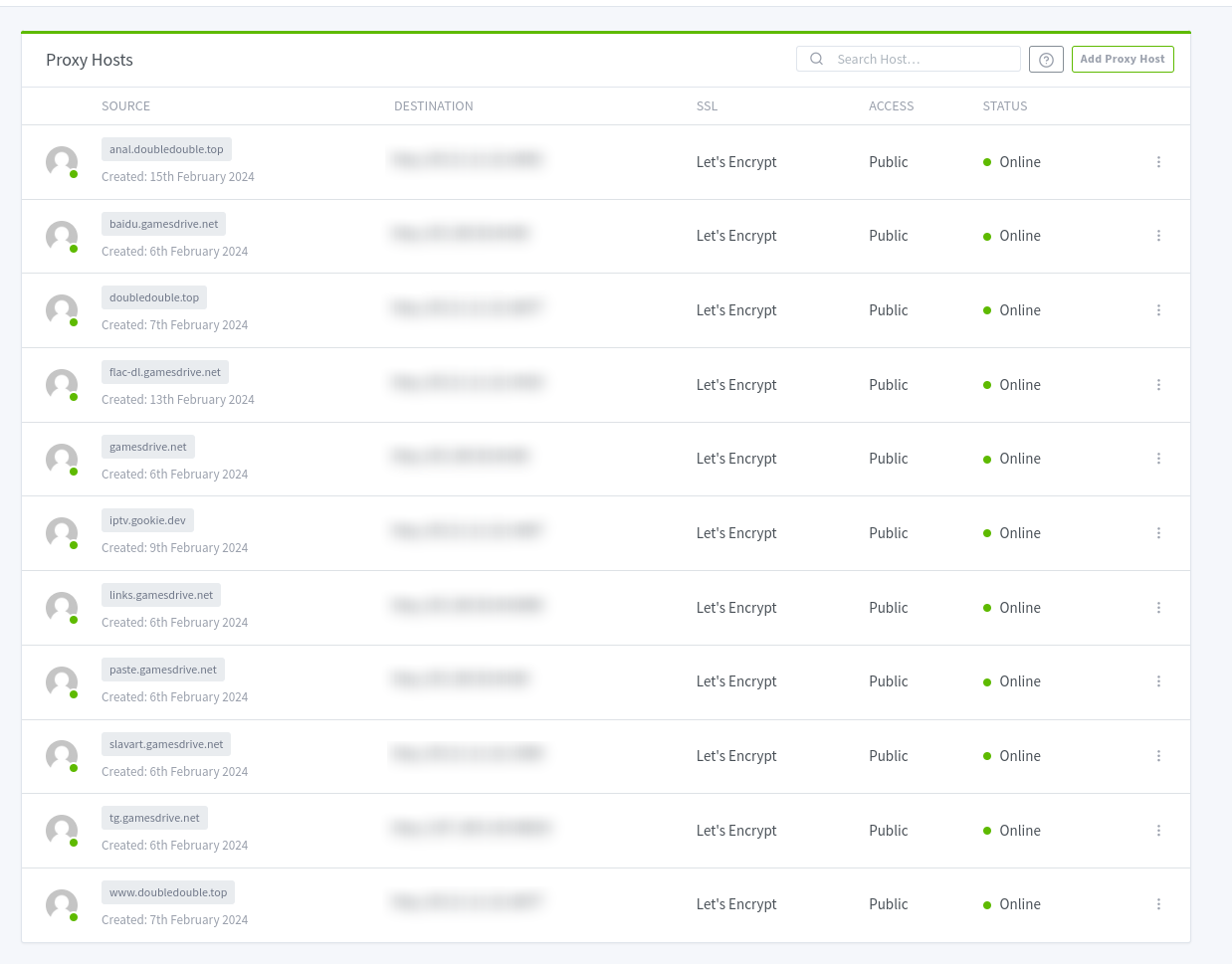 Holy shit, those are the IP addresses to about 11 different hosts, including the homepages for doubledouble.top and gamesdrive.net. Let's point them somewhere else. Since I don't have access to the webserver, I decided to make a Rentry document. But since proxy hosts configuration doesn't let us point to website subdirectories, we are going to turn these to redirection hosts. (I don't have a screenshot of this.)
Holy shit, those are the IP addresses to about 11 different hosts, including the homepages for doubledouble.top and gamesdrive.net. Let's point them somewhere else. Since I don't have access to the webserver, I decided to make a Rentry document. But since proxy hosts configuration doesn't let us point to website subdirectories, we are going to turn these to redirection hosts. (I don't have a screenshot of this.)
Aftermath
Shortly after I did this, people in the Telegram channel started to notice. I didn't think it would happen so soon.
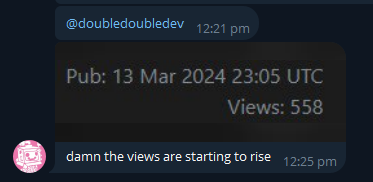 Five hundred views in the matter of minutes, that's pretty good. An admin opens chat and admits they've noticed the issue before but didn't know it was a credential leak. lol
Five hundred views in the matter of minutes, that's pretty good. An admin opens chat and admits they've noticed the issue before but didn't know it was a credential leak. lol
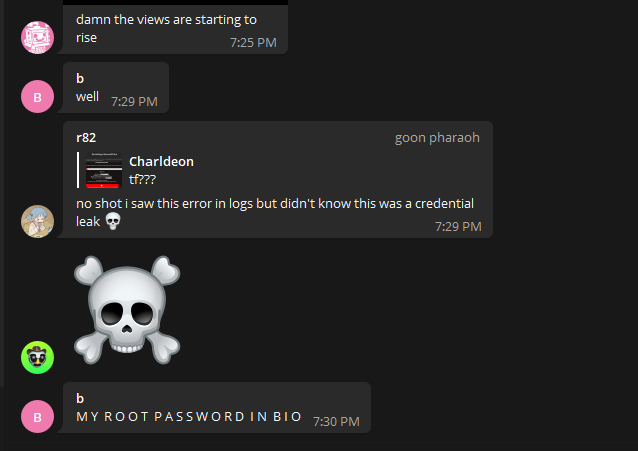 After about 20 minutes and 2.6k Rentry views, the owner changed DNS records, reset everything, and made some Telegram announcements.
After about 20 minutes and 2.6k Rentry views, the owner changed DNS records, reset everything, and made some Telegram announcements.
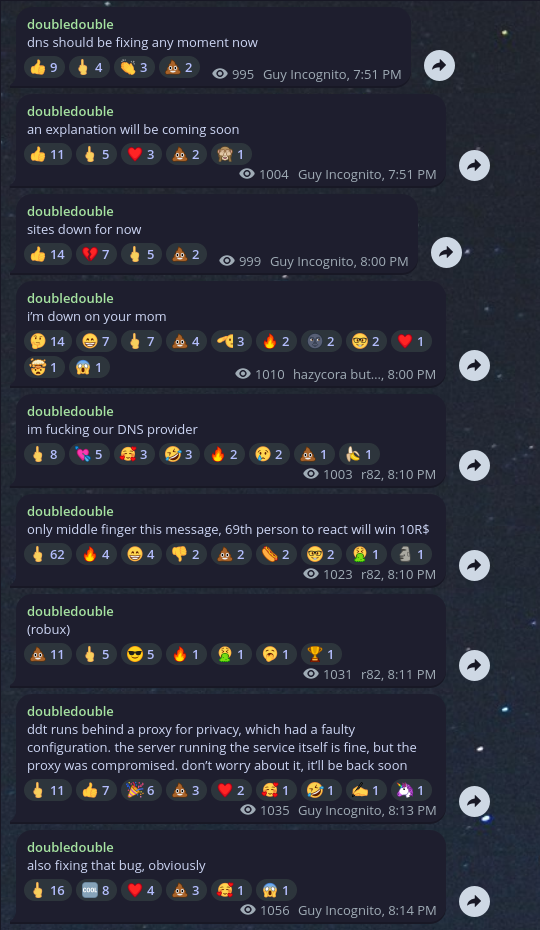 I had a talk with Guy Incognito and r82, they weren't too mad.
I had a talk with Guy Incognito and r82, they weren't too mad.
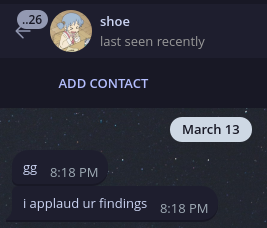 I'm sure they were annoyed though. We do a little bit of trolling ;)
I'm sure they were annoyed though. We do a little bit of trolling ;)